Ransomware, should small businesses worry?
What is Ransomware?
Ransomware is a type of malware attack that encrypts a victim’s files so they can’t access their information, effectively holding their data for ransom. Once a computer network or system is infected by ransomware, cybercriminals encrypt the victim’s files and demand a ransom in exchange for a decryption key. The ransom is usually crypto currency, and the threat is losing data or exposing sensitive information to the public.
Types of Ransomware
There are two main types of Ransomware used in a malware attack:
Locker ransomware locks the users out of their devices. This is the simplest form, and sometimes a cybersecurity expert can restore access.
Crypto ransomware encrypts users’ data. If data is encrypted, it cannot be accessed without a unique decryption key the hackers may or may not have.

Ransomware impact on small businesses
Small businesses are increasingly targeted by ransomware gangs, says a report by ransomware recovery specialists Coveware. Because large companies have a lot of data they are usually the ones that make the news when it comes to ransomware attacks. However according to a study by Coveware a “tactical shift” has been introduced by many ransomware gangs. This includes a “deliberate attempt to extort companies that are large enough to pay a ‘big game’ ransom amount but small enough to keep attack operating costs low as well as taking the attention away from media and Law Enforcement.”
The report notes that 82% of attacks that took place in 2021 impacted organizations with less than one thousand employees. Companies with 11 to 100 employees make up a significant proportion of the overall victims, 37.2%. Even though large companies suffer attacks, small companies are easier targets because of the limit in resources, knowledge, and funding. It is also important to note that studies show that only 65% of ransomware victims actually get their data back, after paying the ransom. The most alarming statistic is that only 57% of companies successfully recovered their data from a backup after the incident.
It is not exactly clear how ransomware gangs decide on the amount of ransom money to demand from their victims. Some just make up a number, but the more organized crime groups researches the victim’s ability to pay. There are many publicly available resources on the dark web that show the financial capabilities of companies.
The ransom demand can fall between $1 000 and $8.4B. Sometimes the price is set so low that when you consider the stress and economic implication of the attack on your business, you may consider it as a “nuisance expense” and pay. Crypto currencies are a preferred payment method as it is very difficult to trace.
All sectors of business are being impacted by ransomware. According to * Netdiligence 2022 spotlight on ransomware the technology sector saw the biggest impact followed by the energy sector.
Many businesses don’t realize that the ransom demand is not the only money they will be paying. Insurance for ransomware is a yearly cost and many small companies don’t have this insurance at all. Then there is the forensic cost that comes to play when the attack is being investigated. Smaller companies might not have the funds to investigate an attack. There could also be regulatory fines that need to be paid. For a small business this could be the reason for bankruptcy and many small companies just are not resilient enough to weather a big ransom attack. The best course of action is to prevent this from happening at all.
How do you prevent an attack?
- Scanning computers with antivirus/antimalware software on a regular schedule.
- Configuring your firewall to prevent ransomware or installing a next-gen Firewall.
- Training your employees in best practices, such as.
- never click on unverified links
- opening only trusted attachments
- be careful in supplying personal information
- limit the use of USB devices
- Backing up your business data on a regular basis, encrypting it and storing it offline.
- Patching your operating system and keeping security patches up to date.
- Filtering emails to prevent spam from reaching employees.
- Limiting the number of administrative privileges given to employees.
- Multi-factor authentication so a compromised password won’t give away your data.
- Installing endpoint security

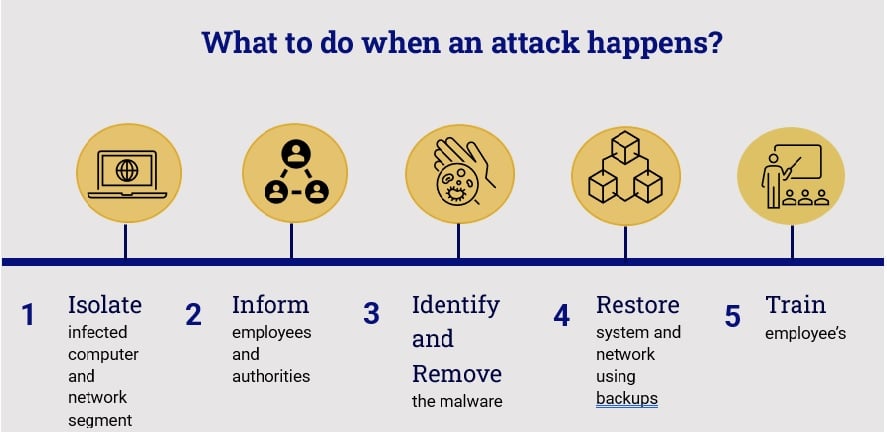
What to do when an attack happens?
Isolate
The first action a business should take is to isolate the ransomware. Shutting down the system prevents the ransomware in spreading to the whole system. Disconnect all cables to and from the device. Wi-Fi should be discontinued to the device and network segment.
Inform
Break the news to employees as this will impact the work environment. Contact your insurance company if you have ransomware insurance as they will be able to assist you in dealing with the ransom payment. Notify your local law enforcement and the FBI.
Identify and Remove
The next step is to identify the type of malware used, whether you decide to pay the ransom or not. You might want to use a specialized company that has experience in malware removal to disinfect your network or system and assist you in recovery. Recovery could take some time and it is important to have a time estimate available to give to your customers that are impacted by this attack.
Restore
You might find that it is impossible to recover the attacked machine or network segment and restoring from backup is the only option. Always restore to a machine that is isolated first to make sure that the last back up has not been infected already. A specialized company can help get your system back online. Once you are back online you would need to change all passwords. You might find that you need to contact your customers at this stage depending on how long your business will be offline.
Train
After the dust has settled a good course of action would be to train your personnel on how to act to prevent an attack as well as how to respond correctly once an attack happens. Discussing how the attack happened so that they have complete insight into the process and why prevention is so important in the war against ransomware actors.
Why should you think twice before paying?
Even after paying your data might not be unlocked. The bad actors might tell you that they will give you a key to decrypt your data, but you don’t know if that key will actually work. The bad actors might return with a counteroffer once you have paid a smaller amount, requesting you to pay an even higher amount.
If you still decide to pay asking for a proof of life demonstration will show you that they can indeed decrypt a file. Paying a ransom amount only encourages the bad actors to continue to exploit innocent victims. Paying the ransom could effectively make you a target for a second attack as you are now labeled as being “willing to pay” and this will attract other bad actors to follow suit.
In Conclusion
Ransomware can bankrupt small companies. Loss of profit due to downtime, cost of the whole attack and the loss of reputation might all be too much for a company with limited resources. Prevention is the key in ransomware attacks and is better than cure. Small businesses should take security seriously, and security starts with training. Employees that are knowledgeable about cyber risks make the workforce stronger and the company more resilient. When budget is a constraint, lock arms with a Cybersecurity company, like Servadus, that can help you set up the necessary prevention, in a budget-friendly way.








