The Assessment Experience in Cybersecurity & Compliance
Those in network operations, security, and audit know that audit fatigue is real. The cybersecurity community is working from one assessment to another for each framework. Some organizations take steps to combine multiple frameworks into a single assessment. Regardless if it is one assessment or several, some steps lead to a better experience for everyone involved. Before addressing the preparation steps, knowing what an assessment is and how it differs from audits is essential.
There are multiple terms for assessments. Likewise, various references exist for compliance, cybersecurity, and risk assessments. The assessment determines the nature of the program under validation. This effort is a type of estimate that differs from an audit. An audit is a stricter inspection that can have an exact match to requirements. A possible outcome is easier to achieve with an assessment that an audit. Where do validations fit into the assessment and audit plan?
Validation is just one aspect of an assessment. And it relates to documents that the assessor or validator reviews or examines. The standard reference to these documents is artifact or evidence. The artifacts include policies, processes, training, announcements, reports, and technical details. Technical details can be reports from the server or information from a single device. The specific information typically is settings or configurations for the device. The person validating is confirming the artifact supports the objective or requirement.
Assessments Approach
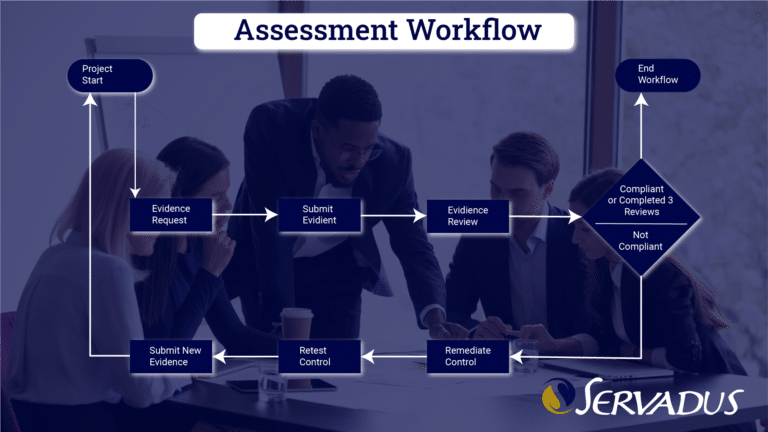
The Servadus method consists of preparation, assessment, and report presentation. The success of the three phases is through the use of a project plan. The assessment phase must also have a workflow.
Each framework has domains and security controls. Each has a few steps to completion. Those steps are requesting evidence, evidence delivery, review, and validation of evidence. In some standards like PCI DSS, If the evidence does not demonstrate the requirement is met, the workflow goes to remediation of the control and starts back at the first step. This process continues until the control is met or in place until the maximum number of remediation attempts is reached, which is usually three. The total number of controls that go to remediation should be no more than ten percent.
Informal, known as GAP assessments, do not go into the remediation part of the workflow. Evidence is provided promptly and validated. In these situations, the evidence demonstrates compliance or a gap in compliance. If no evidence is provided, this demonstrates the people responsible for maintaining compliance do not understand or are incapable of doing so. This also indicates gap compliance.
Before getting too deep into compliance determination, let’s review the details of the three phases.
Preparation
Governance, Risk, and Compliance
Organizations should have a Governance, Risk, and Compliance (GRC) program. Servadus has the GRC tools and expertise to support your program. To learn more about our solution, visit the GRC page. Conducting routine steps such as annual policy review or penetration testing would be two examples of items in the Governance program. General and specific risk assessments are part of continual readiness.
Preparations
Document Collections
Preparing for an assessment ensures the organization can present the scope of systems and data being reviewed and that non-technical documentations are in place for delivery to the assessor team. Policies, processes, risk assessments, background checks, scoping documents, Inventory of in-scope systems, list of Service Providers with their compliance status and contracts, and training records are a good starting point. There is often a misconception the assessor determines how much of the network and people are in scope. The organization must evaluate and understand the scope from the start of the compliance program. Proper Governance that leads to sustainable cybersecurity is only achievable by this understanding. Our team is available to guide the scope of PCI DSS, CMMC, and other programs.
Scoping
The organization under review must present scoping documentation to the assessor for review. The paper is to include the methods used to segment the sensitive data from other systems not part of the environment. For PCI DSS, the protected data is cardholder data (CHD), which is in the Card Data Environment (CDE). If there is no segmentation, then the entire network is the CDE, which we highly discourage. Unlike PCI DSS, CMMC requires the segmentation of FCI and CUI processes and data. This service is another area where the Servadus team can guide on reducing the scope of the environment. Finally, the assessor will review the scope documents and select the technical sample set from the in-scope systems, assuming the environment is large enough.
Risk Assessments and Compensating Controls
You must understand the risk associated with your organization’s program. If not part of the GRC efforts, complete the risk assessment before starting the assessment. Reviewing risk during a cybersecurity or compliance assessment undoubtedly adds stress to your team and can reduce the accuracy of the risk assessment.
PCI DSS is a mature compliance program with defined approaches and tests for the controls. Compensation control needs development if your organization cannot follow the defined approach. Before the assessment period, compensating controls approvals and implementation has to be in place so that the assessor can determine methods described in the Compensating Control worksheet are working as expected. It should be noted that the assessor is not the approving authority of these worksheets. More information is available on the PCI Security Standards Council’s website. If you have QSA for PCI DSS assessments, use our team to avoid conflict of interest, help design a compensating control, and complete the worksheet for approval.
Assessment
Assessment
They are following the preparation phase. The assessment moves to the workflow previously described. Assessors conduct three direct actions during the evaluation portion of the assessment. First, they will review or examine artifacts; second, conduct interviews of people involved; and finally, observe actions taken by the appropriate people. It is common to hear that an assessment evaluates people, processes, and technology. Without a doubt, policy is part of the process in this trilogy. There are times when there is more than one assessor or other team member. The lead assessor is ultimately accountable for assessor activities, even with a project manager coordinating the activities. Regardless of the size of the assessor team, feedback completing evidence reviews. With Servadus, all controls go through a four-step process to ensure your team understands the request for evidence, knows when the evidence went to the assessor, can determine when the evidence review is complete, and see the acceptance of the evidence.
Activities
Interviews include executives, managers, and team members. Actions are simple tasks like checking in a visitor to the building to administrators attempting to use a system default password. Generally, assessors should not operate the systems, have an account of the network environment being assessed, and should be escorted within sensitive areas or with computers logged in.
For a brief insight into your experience of completing self-assessments, watch “The Servadus Experience of Cybersecurity Assessments” video.
The assessment will typically follow the framework and controls. The Servadus Cyber Risk Review has 1 Domain with ten primary questions. CMMC has thirteen domains or Practices with 17 controls. Last but not least, Payment Card Industry Data Security Standards (PCI DSS) compliance for Service Providers and Merchants has 400-plus security controls. The length and complexity of the assessment does vary.
Report Development
Developing the report is a parallel process to the assessment activities. Information entered by your organization’s assessor team or assessment Point of Contact goes directly to the final report. This allows for quicker delivery of the report and findings. General reports are ready for presentation within two business days after completing the evidence review.
Results Presentation
Gap Assessments
Assessments start with the end in mind. Depending on the framework and purpose of the assessment next steps can differ. GAP assessments focus internally and result in a project plan or Plan of Objectives and Milestone (POAM) to remediate the GAPs.
Formal Assessments
The goal of conducting a formal assessment is to demonstrate compliance with a final report and attestation document. PCI DSS and SWIFT CSP require attestation with the assessor’s signature. CMMC Level 1 and Level 2 have different requirements.
Presentation and Next Steps
The Servadus assessor presents the assessment findings and is available to answer the questions. In addition, the assessor can provide next-step recommendations and a project plan with a manager to facilitate post-assessment remediation efforts.







